1. Run GPMC.msc (url2open.com/gpmc) → Right-click "Default Domain Policy" and chose "Edit" → Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → Audit Policy:
- Audit account management → Define → Success
- Audit directory service access → Define → Success.
2. Return to the Security Settings level → Event Log:
- Maximum security log size → Define to 1gb
- Retention method for security log → Define to Overwrite events as needed.
3. Open ADSI Edit (url2open.com/adsi) → Right-click ADSI Edit → Connect to Default naming context → Right-click DomainDNS object with the name of your domain → Properties → Security (Tab) → Advanced (Button) → Auditing (Tab) → Add Principal "Everyone" → Type "Success" → Applies to "This object and Descendant objects" → Permissions → Select all check boxes by clicking on "Full Control", except the following: Full Control, List Contents, Read all properties, Read permissions → Click "OK".
4. Open Event viewer and filter Security log to find event id’s (Windows Server 2003/2008-2012):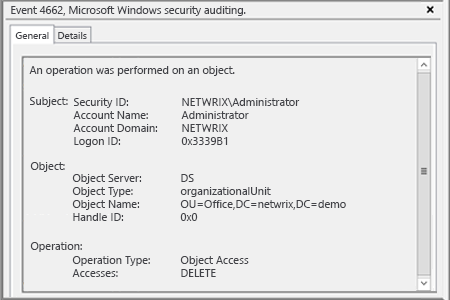
- 631, 635, 648, 653, 658, 663/4727, 4731, 4754 , 4759, 4744, 4749 – Group created
- 632, 636, 650, 655, 660, 665/4728, 4732, 4756 , 4761, 4746, 4751 – Member added to a group
- 633, 637, 651, 656, 661, 666/4729, 4733, 4757, 4762, 4747, 4752 – Member removed from a group
- 634, 638, 652, 662, 667, 657/4730, 4734, 4758, 4748, 4753, 4763 – Group deleted
- 639, 641, 649, 654, 659, 664/4735, 4737, 4745, 4750, 4755, 4760 – Group changed
- 566/4662 - An operation was performed on an object (Type: Directory Service Access).

0 comments:
Post a Comment