A user added to Domain Admins Group receives full control over Active Directory and gets access to IT systems that use Windows authentication, such as System Center Control Manager, SQL Server, SharePoint. Thus a user, added to Domain Admins Group without any valid reason, may cause Active Directory downtime by deleting OUs, shut down a Domain Controller and become a root cause of a security breach by creating backdoor accounts.
Native Auditing
Configure Audit Policy Settings by running GPMC.msc
- Create a new policy and assign it to your domain or edit "Default Domain Policy" → Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → Audit Policy → Audit account management → Define → Success.
Configure object-level Active Directory auditing settings by opening ADSI Edit
- → Connect to "Default naming context"→ Click "OK" → Right-click DomainDNS object with the name of your domain → Properties → Security (Tab) → Advanced (Button) → Auditing (Tab) → Add Principal "Everyone" → Type "Success" → Applies to "This object and Descendant objects" → Permissions: → Select all check boxes except the following: "Full Control", "List Contents", "Read all properties", "Read permissions" → Click "OK".
Enlarge security event log capacity by running GPMC.msc
- → Edit the policy you've created → Computer Configuration → Policies → Windows Settings → Security Settings → Event Log → Define:
- Maximum security log size to 4gb
- Retention method for security log to "Overwrite events as needed".
- Run "gpupdate /force" command.
Filter security log
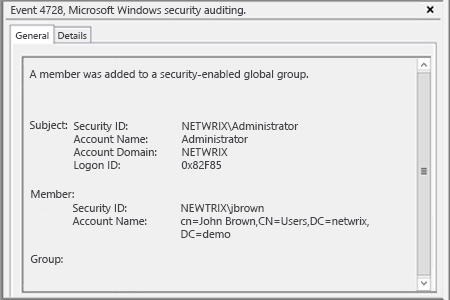
- Run eventvwr.msc and filter security log for event id 4728 to detect when users are added to security-enabled global groups. The group name in our case is "Domain Admins".
0 comments:
Post a Comment